Build Authentication, Access, and Verification for Your Users in minutes
Pelican provides a simple lightweight frontend SDK for authentication, access, and verification.
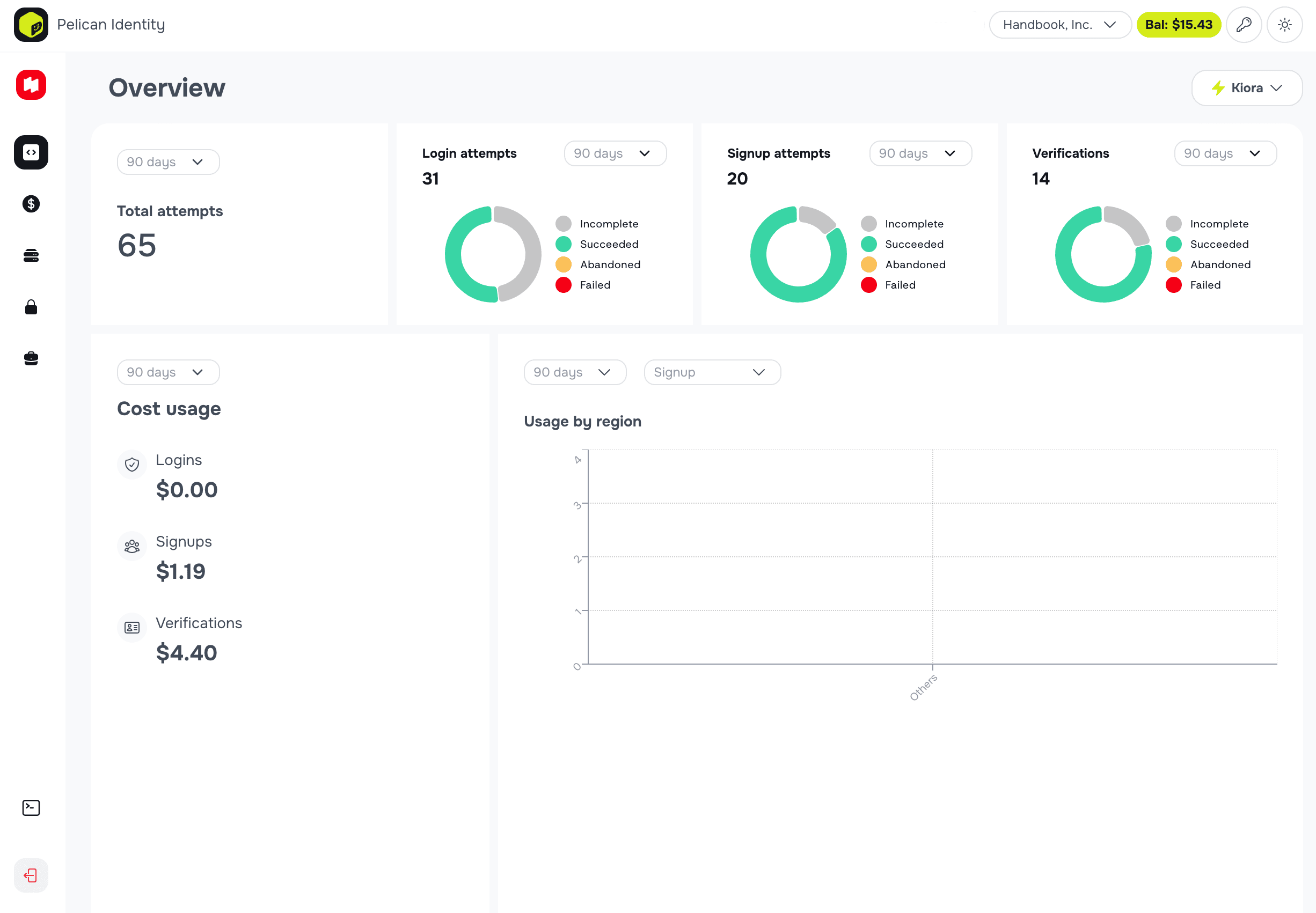
Why Pelican
Instant Authentication.
Passwordless signup and login in under 5 seconds. No OTPs, no magic links, no friction.Compliance Without Headaches.
We handle the entire identity verification flow for you — secure, auditable, and fully compliant.Privacy-First Identity
Deterministic User IDs
Each business gets a unique ID per user. No raw data sharing. Full privacy by default. Users cannot be tracked across apps.Verified Contact Information
Emails and phone numbers are verified automatically via Pelican Vault. No OTP setup, no email confirmation links, no password resets.Consent-Based Data Sharing
Businesses request only what they need (name, DOB, country, etc.) Users approve instantly during sign-in. No extra flows.Instant KYC / Identity Verification
Switch on KYC mode and Pelican Vault automatically handles: Face capture, Liveness detection, ID document verification, Face-to-ID match, Businesses receive compliance-ready identity data instantly.Integration in Minutes, Not Days
Install the Pelican frontend SDK, provide your public key & project key, configure your app from the dashboard, and request the exact data you need — that’s all.
Pelican handles:
Documentations
import { PelicanAuth } from "@pelican-identity/react";
<PelicanAuth
publicKey="pk_xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
projectId="pi_xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"
authType="login"
onError={(error) => console.log(error)}
onSuccess={(identity) => {
sendToBackend(identity);
}}
/>Portable Identity & Secure Recovery
Your Pelican identity is portable, private, and fully owned by you — not locked to any device or platform.
Cryptographic Recovery Phrase
Your Pelican identity is backed by a secure recovery phrase phrase — not a password, not an email, not a device.Restore Identity Anywhere
Switch devices effortlessly. Enter your phrase on a new phone or laptop and your identity is instantly restored.No Email Takeover Risk
Attackers can’t hijack your account through email resets. Your identity is cryptographically protected.Ownership Comes With Responsibility
If you lose your recovery phrase, access is permanently lost — just like secure authentication apps.This is what enables true identity ownership — not platform lock-in.
We Handle the Hard Work of Identity Verification
Skip building your own KYC flow or managing 3rd-party integrations and webhooks. Pelican handles verification, compliance, and proof management so your team can stay focused on your product.
How It Works
A simple, secure flow that gives your users control — and your business verified identity data.
1. Sign In / Scan
Users authenticate instantly with Pelican Vault.
2. Verified Contact Info
Emails and phone numbers are already verified and ready.
3. Consent Sharing
Users approve only the data each business requests.
4. KYC / Compliance
If required, Pelican Vault completes enrollment and delivers verified identity data.
Built for High-Security & Regulated Industries
Pelican is designed for environments where identity failure is not an option.
Use Cases
- Digital banking & fintech
- Lending & investment platforms
- Crypto exchanges
- Regulated marketplaces
- Government & enterprise systems
Enterprise Capabilities
- Deterministic, non-reversible user identifiers
- Zero raw PII exposure to Pelican
- Encrypted relay between user & business
- Device-portable identity via cryptographic recovery
- Full audit trails
- Face match, liveness & document verification
You get compliance, security, and privacy — without storing sensitive identity data yourself.
The Trust Layer Your Business Can Rely On
Pelican is built with regulatory alignment and auditability at the core.
GDPR aligned
Consent-first architecture
Data minimization by design
Business remains the data controller
Audit logs available for compliance review
For Businesses
Reduce friction, improve security, and cut costs
Reduce onboarding drop-off by up to 60%
Save significantly on KYC costs
Eliminate password and OTP management
Deterministic IDs remove breach risks from leaked emails & passwords
No raw user identity storage on your servers
Privacy-Centric Architecture. Security at Every Layer.
Built for individuals and enterprises who require trust by default.
For Users
Share only what you choose
Cannot be tracked across apps
Data lives locally inside Pelican Vault
Encrypted end-to-end
For Businesses
End-to-end encrypted attribute relay
Pelican never stores raw user identity data
Only you and your user see the identifying data
Breach surface is minimized by architecture


